Tips & Tricks for Managing Privacy Settings
Delete when done
Many of us download apps for a specific purpose, such as before a airline flight or a trip. It’s a good security practice to delete all apps you no longer use.
Review both Privacy Statements and settings
Privacy statements are required by law in many states and should answer fundamental questions:
- What personal information is collected?
- How is the information collected?
- Why is the information collected?
- How will the information be used?
- Who will have access to the information?
- What are your options?
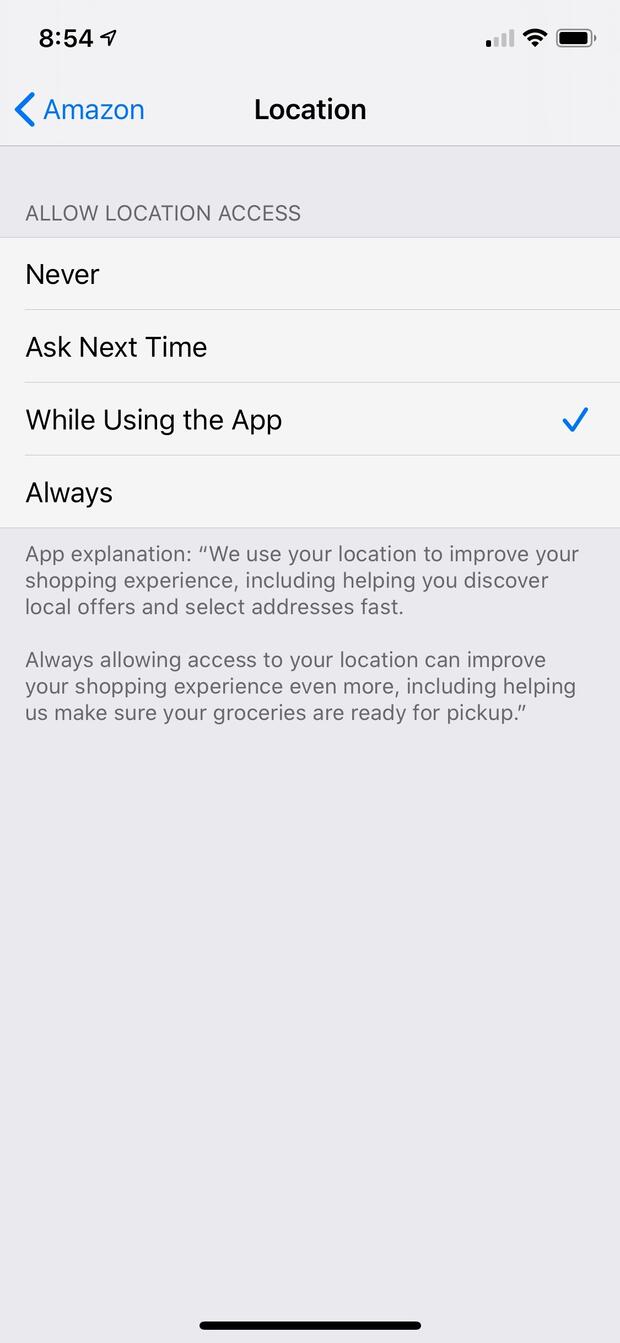
While the privacy statement will outline the privacy practices of an organization, the privacy settings will give you control over how the data is shared. For example, does the Amazon app on your phone really need to know your location at all times?
Make it a habit to review these settings early and often.
Keep it updated
Your phone and applications are just as vulnerable as your physical computer. It’s important to be sure to update promptly as this is your best defense against cyber-attacks.
Passwords are important here, too
A strong passphrase is a sentence or passphrase that is at least 12 characters long. Focus on positive sentences or phrases that are easy to remember. Connected devices and applications still contain information about you and your habits. It’s important to make sure that is just as protected as you would other sensitive data. Be sure to utilize multi-factor authentication (MFA) when offered. MFA uses a second piece of information in addition to a password, such as a pin number or token, to verify a user’s identity before granting access.
Remember, less is more
Think about what your putting online as it’s difficult to have information removed once it’s been posted. This goes for social media sites as well as applications and services requesting information about you. If it isn’t required, consider leaving it blank. And if a company does require information you don’t feel comfortable submitting, then reconsider creating a profile with that company.
Contact
Online
Address
| Date published: | May 5, 2020 |
|---|