December
DHS confirms state-sponsored cyberattack on public sector IT-service providers
PUBLISHED: Dec. 13, 2020
SolarWinds, a major provider of network management systems (NMS), is said to be the victim of a highly sophisticated, state-sponsored cyberattack. The attackers, believed to be operating under the auspices of the Russian Federation’s Foreign Intelligence Service, were able to successfully deploy a malware-infected update to the company’s Orion Network Performance Monitor.
SolarWinds ubiquity in the field of NMS may turn out to be problematic - the company has more than 300,000 customers worldwide, including more than 400 of the US Fortune 500 companies and is utilized across five branches of the US military and the Departments of Defense, State and Justice, as well as the Office of the President. Intrusions have already been detected at the US Treasury Department as well the US Department of Commerce's National Telecommunications and Information Administration (NTIA). Though not officially confirmed, major US publications have cited sources claiming that multiple other government agencies have been impacted in the attack.
Late Sunday night, following confirmation of the successful attack on the Commerce Department, the cybersecurity arm of the Department of Homeland Security issued an Emergency Directive calling on "all federal civilian agencies to review their networks for indicators of compromise and disconnect or power down SolarWinds Orion products immediately."
Sources speaking with the Washington Post linked the intrusion to APT29, a codename used by the cyber-security industry to describe hackers associated with the Russian Foreign Intelligence Service (SVR).
Source:
- CISA
November
ALERT: Commonwealth Employees Targeted by Phishing Campaign
PUBLISHED: Nov. 13, 2020
Colleagues,
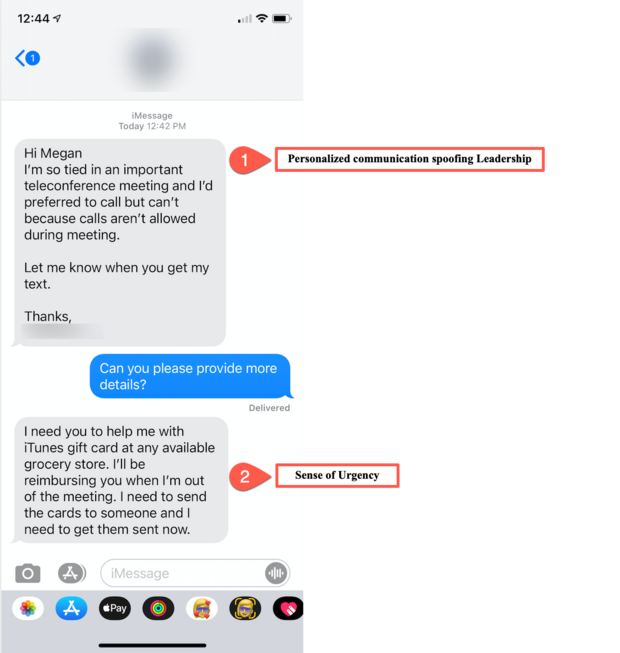
As many of you are aware, the Commonwealth has recently been the target of an aggressive phishing and smishing campaign. The malicious actors are using free e-mail services, such as g-mail, to create fake e-mail accounts designed to impersonate Commonwealth Leadership and are using social engineering tactics to elicit a sense of urgency. In addition to e-mail, the scammers have started using text messages as another way to phish our community. This technique, often referred to as smishing or SMS phishing, is a text-message based variation of traditional phishing scams, and a growing cyber threat. This particular campaign does not contain any links or malicious documents, but rather requests that the user purchase a gift card on behalf of the executive.
The EOTSS Messaging and Security Teams are aware of the situation and are working to block incoming messages. However, we ask that you remain vigilant. If you receive an e-mail or a text message requesting you to purchase a gift card, to pay by gift card, or to wire money – for any reason – that’s a sure sign of scam. Any correspondence, whether e-mail or SMS-based, imploring (or even threatening) the need for an immediate response, should be treated with healthy skepticism.
Remember to pay attention to key warning signs:
-
False sense of urgency
-
External e-mail address as either the sender or the reply-to address
-
Misspellings and Typos
-
Consider the purpose; is this someone you’d typically correspond with?
-
Be wary of suspicious attachments and links
As always, suspicious messages or phishing e-mails can be reported to the EOTSS End User Service Desk or your local Agency IT Support via the contact information below.
Online
EOTSS End User Service Desk
Log in to ServiceNow
MassGov@service-now.com
Phone
EOTSS End User Service Desk (844) 435-7629
24x7x365 support for Commonwealth end users
CommonHelp IT Service Desk (866) 888-2808
for agency/Secretariat IT help desks and support personnel
We appreciate your continued cooperation. Please do not hesitate to reach out with any questions or concerns.
Sincerely,
John Merto
Commonwealth Chief Information Security Officer
Executive Office of Technology Services and Security
October
Ransomware Activity Targeting the Healthcare and Public Health Sector (CISA Alert AA20-302A)
PUBLISHED: Oct. 28, 2020
The Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the U.S. Department of Health and Human Services (HHS) have credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.
CISA, FBI, and HHS have released AA20-302A Ransomware Activity Targeting the Healthcare and Public Health Sector that details both the threat and practices that healthcare organizations should continuously engage in to help manage the risk posed by ransomware and other cyber threats. The advisory references the joint CISA MS-ISAC Ransomware Guide that provides a ransomware response checklist that can serve as a ransomware-specific addendum to organization cyber incident response plans.
It is suspected that the attacks are being launched by Eastern European hackers that targeted U.S. hospitals, media reported Wednesday. Experts said the likely group behind the attacks was known as Wizard Spider or UNC 1878. They warned that such attacks can disrupt hospital operations and lead to loss of life. Federal authorities said the recent attacks include incidents in Oregon, California, and New York.
CISA, FBI, and HHS are sharing this information in order to provide a warning to healthcare providers to ensure that they take timely and reasonable precautions to protect their networks from these threats. CISA encourages users and administrators to review CISA’s Ransomware webpage for additional information.