How Internet of Things Devices Communicate
To operate and communicate data, Internet of Things (IoT) devices must be interconnected. The United States Government Accountability Office authored an assessment regarding the IoT in July 2017 titled Internet of Things: Status and implications of an increasingly connected world (GAO-17-75). This document provided a high-level understanding of the various ways IoT technology might be deployed from four basic architecture models: device to device, device to cloud, device to gateway, and cloud to cloud. The diagrams below, taken from GAO-17-75, depict the four models.
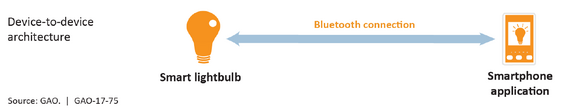
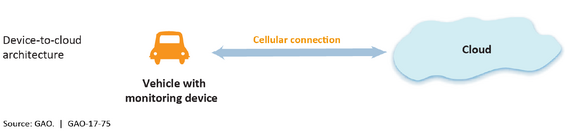
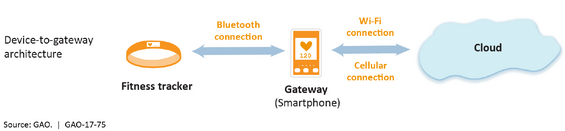
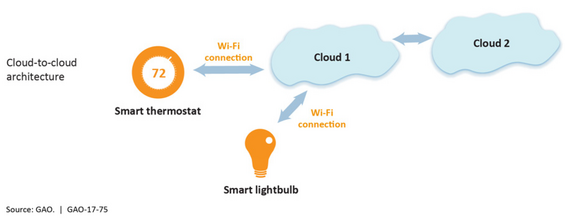
IoT in the Commonwealth
To obtain a better understanding of the current use of IoT devices by state agencies, the Office of the State Auditor conducted a survey of 84 state agencies, 28 of which responded. The purpose of this survey was to determine the current and future plans for deploying IoT devices in the Commonwealth, the types of IoT devices deployed, the ways information technology (IT) devices are connected to networks, the ways IoT devices are used, and agencies’ perspectives on the benefits and risks of IoT technology.
For the purpose of our survey, we identified four types of IoT devices used, referred to as “waves” in this report. These waves are defined in a January 15, 2014 paper published by the SysAdmin, Audit, Network, Security (SANS) Institute, Securing the “Internet of Things”:
- PCs, servers, routers, switches and other such devices bought as IT devices by enterprise IT people, primarily using wired connectivity
- Medical machinery, [supervisory control and data acquisition], process control, kiosks and similar technologies bought as appliances by enterprise operational technology (OT) people primarily using wired connectivity
- Smartphones and tablets bought as IT devices by consumers (employees) exclusively using wireless connectivity and often multiple forms of wireless connectivity
- Single-purpose devices bought by both consumers, IT and OT people exclusively using wireless connectivity, generally a single form
The most significant responses received from our survey include the following:
- All agencies were using general technology from the first wave of the IoT, and 24 out of 28 agencies were using third-wave devices such as smartphones and tablets. Five agencies indicated that they were using fourth-wave IoT devices, and 3 were using second-wave devices.
- Various agencies have different plans for using the IoT: 12 indicated that they planned to expand use, and 11 indicated that they did not have IoT plans currently but might in the future. Three agencies stated that they were not considering a plan for using the IoT.
- Nineteen out of 28 agencies believed that IoT consumer devices were available in the marketplace that could enable them to better manage a particular problem area. However, 8 of those 19 respondents also indicated that IoT devices that were relevant to the agencies were not yet available. Additionally, 5 agencies stated that they did not know if they were ready to adopt IoT devices.
- There were also differing opinions on adopting IoT technology. Twelve agencies agreed that IoT technology was in its infancy and the risk of adopting the use of IoT devices was greater than the benefits. Eleven agencies disagreed with these statements. Four agencies were unsure, and one did not answer.
- When asked about whether IoT technology risk could be effectively and efficiently managed by the current controls, 11 agencies said “yes,” 13 said “no,” 3 did not know, and 1 did not answer.
- Information that is collected at organizations includes data about energy and utilities, technology, consumer products and services, financial services and real estate, government, and healthcare and life sciences.
- There could be various effects at the agencies if IoT devices did not operate properly for a prolonged period, including program interruption (acknowledged by 12 agencies), financial effects (9 agencies), and public-safety issues (5 agencies).
There are no specific Massachusetts laws and/or regulations regarding the standardization of IoT use in the public sector. Rather, each Commonwealth agency is allowed to make its own business decisions in this area. Our survey results indicate that there is a lack of unity across the state. As previously discussed, the Executive Office of Technology Services and Security (EOTSS) is in the process of replacing the Massachusetts Access to Government Network with the One Network initiative, which will consolidate the specific agency networks into one centrally managed Commonwealth network. At the time of our audit, EOTSS was aware of the IoT; however, it did not provide any services to Commonwealth agencies regarding smart sensors or other IoT devices.
IoT Use by Commonwealth Agencies during the Audit Period
The Division of Capital Asset Management and Maintenance currently oversees the Commonwealth Building Energy Intelligence (CBEI) Program. The objective of this program is to measure energy use in state buildings and provide decision-makers with information that could be used to reduce energy use. The program includes participants from a significant number of state colleges and universities, state correctional facilities, state hospitals, trial courts, major state office buildings, water treatment facilities, power plants, and other sites. Currently, the IoT is used in smart building management3 within energy information systems to better understand when and how energy is used, identify cost-saving opportunities, and proactively maintain capital assets.
In the CBEI Program, agencies can use the collected data to monitor energy use from one period to the next and modify their building environmental systems to reduce energy use and carbon emissions, resulting in reduced costs as well as environmental benefits.
The next phase of the Commonwealth’s smart building management initiative is to integrate the energy information system with an automated building control system at select sites to enhance energy savings performance. According to the US Department of Energy’s Federal Energy Management Program, the United States federal government is one of the largest energy consumers in the world.
The Massachusetts Department of Transportation (MassDOT) Highway Division provides another example of IoT use. MassDOT has laid an infrastructure of fiber-optic cable underground to provide hardwired local area network connections to roadway surveillance cameras as well as motorist information signs placed along roads (depicted in the Photos section of this report).
In addition, cameras are used in electronic toll collection, which has eliminated tollbooths that hindered traffic flow. Drivers without transponder boxes have their license plate information gathered by IoT sensors and are billed based on the vehicle registration information. There are also electronic toll gantries on the Massachusetts Turnpike, which collect all-electronic tolling, take photos of license plates, and capture vehicle speeds. Photos of toll gantries are shown in the Photos section of this report.
IoT technology is also used by the Massachusetts Bay Transportation Authority (MBTA), the Department of Transitional Assistance (DTA), the Department of Public Health (DPH), and the Department of Environmental Protection (DEP). The MBTA uses global positioning system devices on trains to provide their locations and estimate their times of arrival at stations, which improves communication with riders.
DTA allows people to track their benefits with a phone application that lets them manage their cases, appointments, and contact information and check their balances.
DPH uses patient-monitoring systems in the intensive care unit at the Lemuel Shattuck Hospital to support decision-making and help improve patient care using a wired connection.
DEP uses sensors to collect data and measure air quality to track potentially harmful gases, particles, and toxins. DEP’s MassAir Online website allows users to click on a state map to find real-time air quality data from DEP.
IoT Challenges
According to our interviews with IT professionals, the major IoT challenges facing the Commonwealth are cybersecurity, privacy, connectivity, and a lack of laws and regulations regarding the use of IoT technology. A cybersecurity attack such as a data breach or a denial-of-service attack4 can affect the social, political, and economic wellbeing of a particular person, organization, or government and, according to our survey, can be conducted for various reasons, such as financial gain, malicious intent, recognition, or revenge.
Every device that is connected to an organization’s network increases the opportunities for it to be attacked by a hacker. According to a 2016 PricewaterhouseCoopers5 survey on information security breaches, the question is not whether a data breach will occur, but when. Anything that has an Internet Protocol address could be hacked. As the world becomes interconnected, cybercriminals have more opportunities to perform cyberattacks.
The IoT also poses challenges related to laws and regulations; for example, manufacturers are not required to implement a certain level of security in their IoT devices. This has caused devices to be susceptible to compromise by potential hackers.
| Date published: | September 5, 2018 |
|---|